Identity and Access Management (IAM) has become a central component of any modern architecture. Authentication, user management, access control, regulatory compliance: these building blocks are critical, yet their implementation and long-term operation often remain complex.
To address these challenges, Clever Cloud launched IAM Keycloak as a Service in spring 2025, in partnership with Please Open It, a company specialized in Keycloak integration and expertise. This collaboration made it possible to design a managed service aligned both with open source best practices and with the real-world constraints of production environments.
Since its launch, Keycloak as a Service has evolved significantly to meet the concrete needs of businesses and the requirements of operating IAM at scale.
A Managed Keycloak, Built for Production
Keycloak as a Service is based on a simple approach: delivering the full functional richness of Keycloak without requiring teams to handle infrastructure, maintenance, or monitoring.
The service is natively integrated into the Clever Cloud Console. It therefore becomes a fully-fledged component of the platform, managed from a single control point, just like our other managed services.
Secured Multi Instances: High Availability and Scalability
One of the major evolutions is Secured Multi Instances. It enables Keycloak to be deployed in a clustered setup with multiple nodes, ensuring load distribution and high availability for a critical component such as IAM.
This architecture strengthens service continuity and the ability to handle increased traffic, while meeting the standards expected in production environments. Configuration and management of this architecture are directly accessible from the Clever Cloud Console.
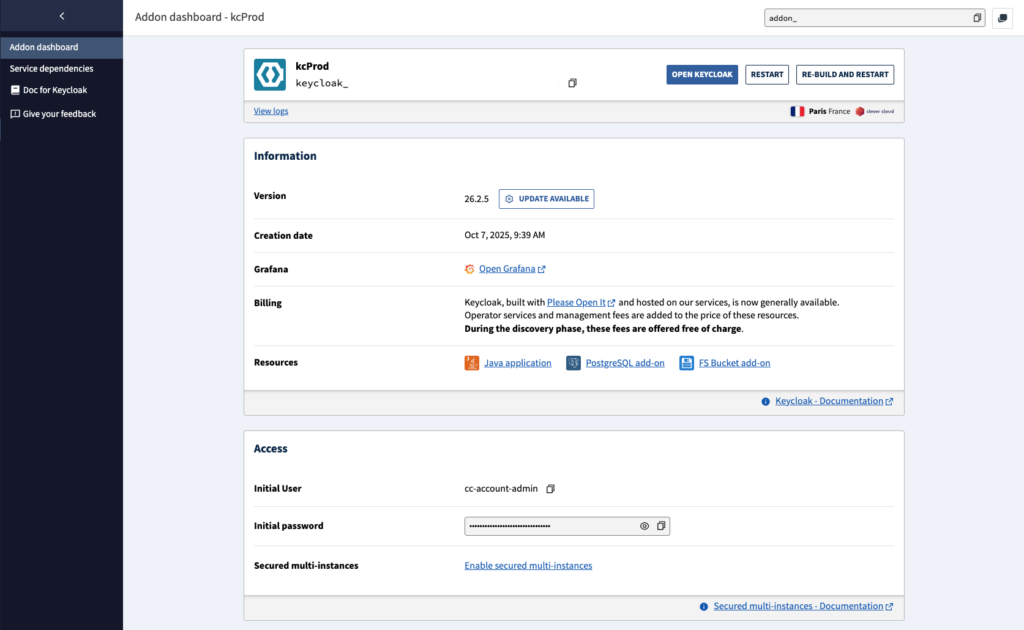
A Dedicated Dashboard in the Console
A Keycloak dashboard is now available in the Clever Cloud Console. It centralizes the service’s essential information along with common administrative actions, making day-to-day management simpler and avoiding the need to juggle multiple tools.
Built-in Monitoring, Included
Monitoring is natively integrated into the service. Operational visibility is immediately available, with no additional configuration or external tools required.
This integrated approach simplifies operations while maintaining a high level of control over how your IAM runs.
Continuous Maintenance and Updates
Managed Keycloak is kept up to date. Recent Keycloak versions are made available as the product evolves, with no operational burden on the customer side.
This ensures access to security patches and functional improvements without heavy or risky upgrade projects.
Simplified addition to your applications
A more structural development concerns Request Flow, a technical foundation that makes it easier to use tools to secure access to your applications, including OAuth2-Proxy.
The latter is compatible with Keycloak, and its configuration is simplified on Clever Cloud. This allows you to implement authentication upstream of the application without modifying the application code. It is particularly well-suited for securing existing applications, back-offices, internal tools, or exposed services.
To Go Further
To present these evolutions in detail, share the technical choices behind them, and answer questions, a live session on Twitch and YouTube is scheduled for February 26 at 1:00 PM. It will be hosted by Horacio Gonzalez (Clever Cloud), joined by Mathieu Passenaud (Please Open It).
It will be an opportunity to take a concrete look at how our managed Keycloak works and to discuss real-world IAM use cases in production environments.







